Git clients and SAML in EasySSO
From version 4.1.5.4 EasySSO supports SAML in Bitbucket.
Unfortunately, there are no git clients (command line, IDE-integrated or GUI ones e.g. SourceTree or TortoiseGit) that support SAML for authentication. As such, EasySSO for Bitbucket explicitly ignores /scm/* URI in SAML authenticator, thus not even attempting SAML authentication for git operations.
If only SAML authentication is enabled in EasySSO, when using command-line or IDE-integrated or GUI tools your users will either have to:
- use SSH key for authentication or
- create personal access tokens or
- use their regular credentials.
However, all these clients support NTLM and Kerberos.
This opens a possibility of offering Kerberos/NTLM SSO to the git clients while doing SAML in the UI by specifying a user-agent allowlist in Kerberos/NTLM Authenticator's/Advanced Configuration/User Agent Filtering Configuration either via "User Agent Rules" (simply capture some git client UA strings and run them through the instant parser that is present on the same page) or via "User Agents Regexps to Ignore" by using a negative match regex e.g. something like:
^((?!git\/).)*$
Git clients and NTLM/Kerberos in EasySSO
If you are using NTLM/Kerberos authenticator in EasySSO with Bitbucket the following tips will help you set up your single sign-on for GIT clients.
Global setting since git 2.11.x
GIT 2.11.x has introduced a bug in NTLM authentication, this global setting enables the old behaviour.
git config --global http.emptyAuth true
URL notation
For NTLM or Kerberos authentication to work your git remote HTTP URLs need to use the following notation http://:@host/repopath.
The ":" in front of "@" tells git to use OS default credentials, i.e. use NTLM or Kerberos when challenged.
Example
https://yourcompany@bitbucket.mycompany.org/scm/bus/project.git
becomes
https://:@bitbucket.mycompany.org/scm/bus/project.git
You can see the current remote URL with the command:
> git remote -v origin https://bitbucket.mydomain.com/scm/proj/your-repo.git (fetch) origin https://bitbucket.mydomain.com/scm/proj/your-repo.git (push)
And you can change it with the command:
> git remote set-url origin https://:@bitbucket.mydomain.com/scm/proj/your-repo.git
After this all git operations on this repository should not request the user to supply credentials – instead, their domain credentials should be used automatically.
In Bitbucket UI, EasySSO can be configured to offer HTTP/HTTPS clone URLs first with the URL automatically rewritten for NTLM/Kerberos SSO – this option is available in EasySSO/NTLM/Advanced Configuration.
Windows command line GIT
Cookies need to be enabled to work around some issues with the push command.
Use the following line to enable cookies:
git config --global http.cookiefile <absolute path to cookie file>
Example
git config --global http.cookiefile C:\Users\yourcompany\git-cookies.txt
Kerberos headers
We do recommend configuring Kerberos to be used – NTLM is great and will still be used when Kerberos is not possible (e.g. on VPN), but it is a 3-step protocol where the client goes back and forth with the server 3 times, while Kerberos is more efficient being a 1-step protocol.
Please note: When using the Kerberos protocol browser sends a relatively huge volume of information in HTTP request headers.
Due to other configurations that may be present in your organisation- the cumulative total size of information may cross the threshold configured for the Atlassian application (usually 8Kb). This usually manifests itself with blank pages being returned once Kerberos starts working. If you are getting this please change the maximum size of the header allowed:
- for JIRA and Confluence and older Stash/Bitbucket - look for Connector elements in server.xml usually located in /conf directory of the installation (not the HOME directory) and increase or add the value for maxHttpHeaderSize. You can start by simply doubling the default 8192 to
<Connector port="80"
maxThreads="150"
minSpareThreads="25"
connectionTimeout="20000"
enableLookups="false"
maxHttpHeaderSize="16384"
protocol="HTTP/1.1"
useBodyEncodingForURI="true"
redirectPort="443"
acceptCount="100"
disableUploadTimeout="true"
bindOnInit="false"/>
- for Bitbucket 5.1+ add the following to bitbucket.properties
max-http-header-size=16384
If you want to stop GIT clients from NTLM/Kerberos SSO
The following steps show you how to configure your EasySSO installation if you:
- Don't want your git clients attempting single sign-on, but
- Want all other attempts to get SSO, such as developers using browsers to access the repository for reviews or commenting on code.
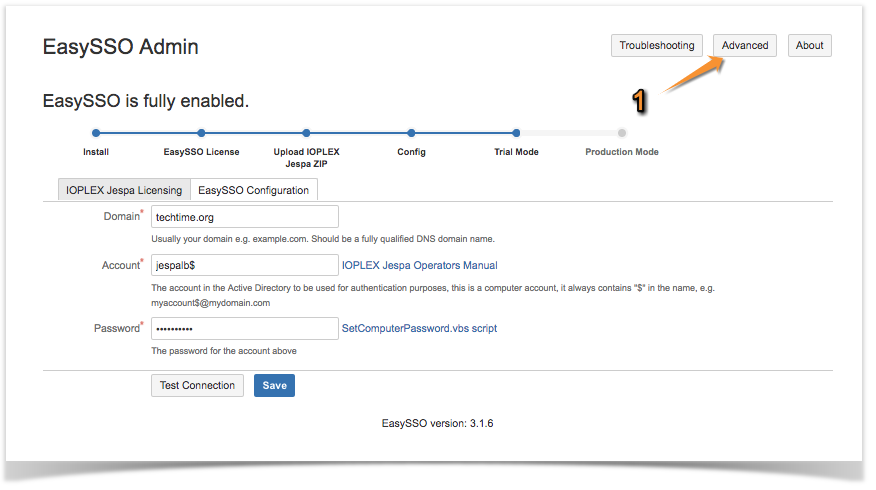
- Go to the EasySSO configuration screen
- On the top right-hand side of the screen click on "Advanced"
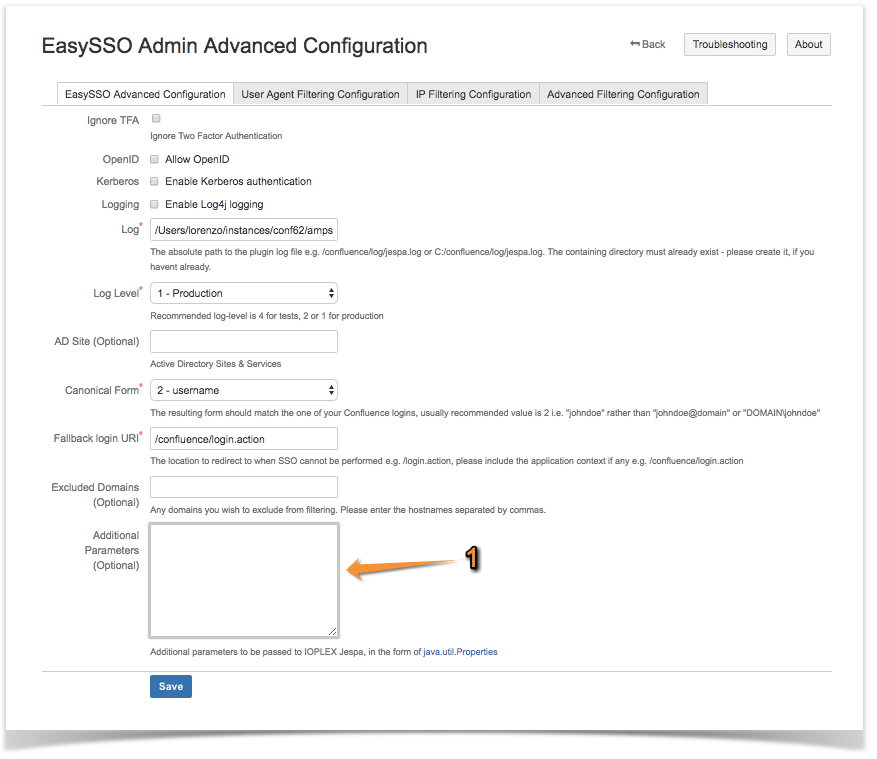
- In the "Additional Parameters" section enter the following line:
excludes=/scm/* - Click on "Save"
This will stop all GIT clients from attempting single sign-on, but will allow SSO via browsers.