EasySSO supports both allowlists and blocklists to allow you to control which client machines will be permitted to use single sign-on.
Important
If a client machine's IP is matched using the allowlist and blocklist, then it'll be treated as allowlisted.
Why do I need this?
If you have external users that don't use your internal AD, then you want to make sure to disable EasySSO for these users, as seamless SSO would fail and they would be prompted for username and password that would always fail.
For example, you would normally disable EasySSO on a guest WiFi, as it's very unlikely that the guests would be using your internal credentials.
EasySSO also needs to be disabled for automated solutions, for instance a wallboard reporting service, that uses a service account to authenticate itself.
If you are part of a large organisation with two sub-nets/divisions and if you didn't want to offer EasySSO to one, you can use filtering by IP sub-net. For example, as a result of a merger, normally the separate domains would trust each other, and users from one domain would be allowed to access the services in another domain, and SSO will succeed but if this is not the case IP Filtering will allow you to segment the network and offer SSO only to one domain.
Allowlist or blocklist client machines
EasySSO 4.0 +
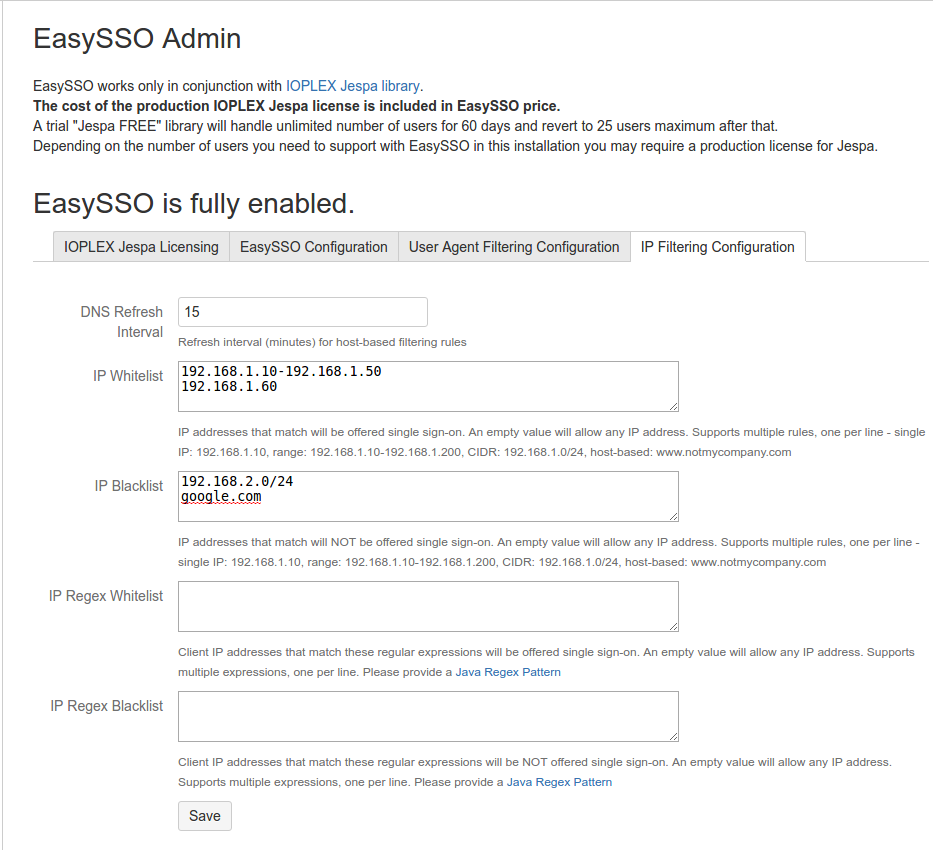
- In the EasySSO configuration screen click NTLM/Kerberos.
- Click 'Advanced Configuration' on the top-right and switch to the 'IP Filtering Configuration' tab.
EasySSO prior to 4.0.0
- In the EasySSO configuration screen switch to the "IP Filtering Configuration" tab.
Create IP or hostname based rules (supports multiple rules, one per line)
Enter individual IP, IP ranges, networks (CIDR notation) or hostnames.
Important
If a client machine's IP is matched using the allowlist and blocklist, then it'll be treated as allowlisted.
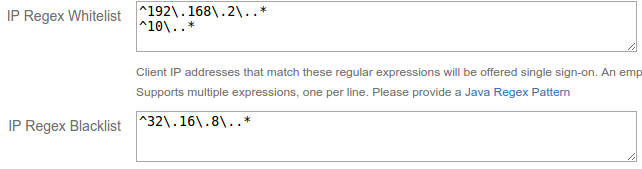
Alternatively – use regular expressions
The allowlist and blocklist can also be configured using Java regular expressions, which allows an even more flexible way to define rules matching IP addresses.
Important
If a client machine's IP is matched using the allowlist and blocklist, then it'll be treated as allowlisted.
DNS Refresh Interval / Host based filtering rules:
For convenience, EasySSO allows hostnames to be specified in both allowlist and blocklist. The actual filtering is done based on IP addresses, so EasySSO must look up the hostname in DNS before it can apply the filters.
EasySSO caches the results of the lookup to reduce the load on the DNS service and minimise delays associated with DNS lookups. The DNS Refresh Interval defines how long the EasySSO should rely on the cached entires before it updates them from DNS.